Imagine your organization’s website is suddenly defaced with offensive content. Customer records disappear without a trace. Core systems grind to a halt. There’s no ransom demand, no explanation—just disruption.
This is what happens if you are a target of cyber vandalism.
Unlike ransomware or phishing attacks, cyber vandalism is not driven by financial gain. These acts are malicious, often random, and designed to inflict reputational and operational damage.
| “Cyber vandalism is the digital world’s version of smashing windows — but the damage goes far deeper.” – Jason Sondhi, CEO, EXOS IT |
Beyond the technical damage, the reputational consequences are significant. 48% of consumers say they would avoid working with an organization that suffered a public data breach.
In this blog, we’ll explore what cyber vandalism is, the tactics used and how you can protect your organization from becoming the next target.
What is Cyber Vandalism?
Cyber vandalism refers to the intentional defacement or destruction of digital assets without the intent of financial gain. Unlike ransomware attacks that demand payment, cyber vandals often act out of malice, political motives, or simply for the thrill.
Nord VPN defined Cyber vandalism as a destructive cyberattack without any obvious profit or ideological motive. Cyber vandals can deface websites, disrupt your organization’s services or delete databases.
Understanding the motives and methods behind these attacks is the first step in building effective defenses.
The Many Faces of Cyber Vandalism: Types and Tactics
Cyber vandalism is a shapeshifter — it doesn’t come in one predictable form. From digital graffiti to full-blown sabotage, its impact is only limited by a bad actor’s imagination and your cybersecurity posture. Here are some of the most common (and most damaging) tactics used in cyber vandalism today.
Website Defacement
This is the most visible form of cyber vandalism. In a typical attack, hackers break into your web server and replace your homepage or internal pages with unauthorized content — often offensive, politically charged, or embarrassing. In high-profile cases, they may insert disturbing images or statements, undermining brand trust in seconds.
Take, for example, the Wikipedia cyber vandalism incident that disrupted the online encyclopedia’s pages, including replacing legitimate content with falsehoods.
Take Cybersecurity Seriously — Partner with EXOS IT |
Data Deletion or Corruption
Here, the damage goes beyond appearances — it hits the heart of your operations. Cyber vandals might erase entire databases, modify sensitive information, or inject corrupted code into your systems. This can paralyze internal processes, derail customer transactions and lead to hours — if not days — of downtime while recovery teams scramble to restore order.
Denial-of-Service (DoS) Attacks
A DoS attack floods your servers or network with a tsunami of traffic, consuming all available resources until your systems grind to a halt. Think of it as a digital traffic jam — one intentionally created to prevent legitimate users from accessing your services.
Unlike DDoS attacks aimed at extortion, cyber vandals who launch DoS attacks often do so simply to cause chaos and reputational damage.
Malware Insertion
Cyber vandals sometimes deploy malware to corrupt systems, alter files or create persistent backdoors for future sabotage. Unlike advanced persistent threats (APTs), which are stealthy and strategic, malware from vandals tends to be loud, destructive and disruptive.
Common examples include website-crippling worms, file-encrypting viruses or malicious scripts that lock users out. Since malware can be delivered through compromised websites, email attachments or even USB devices, your risk surface is broader than you think.
Each of these tactics has the potential to severely disrupt an organization — not just operationally, but financially and reputationally.
| Explore More of Our Leading Insights |
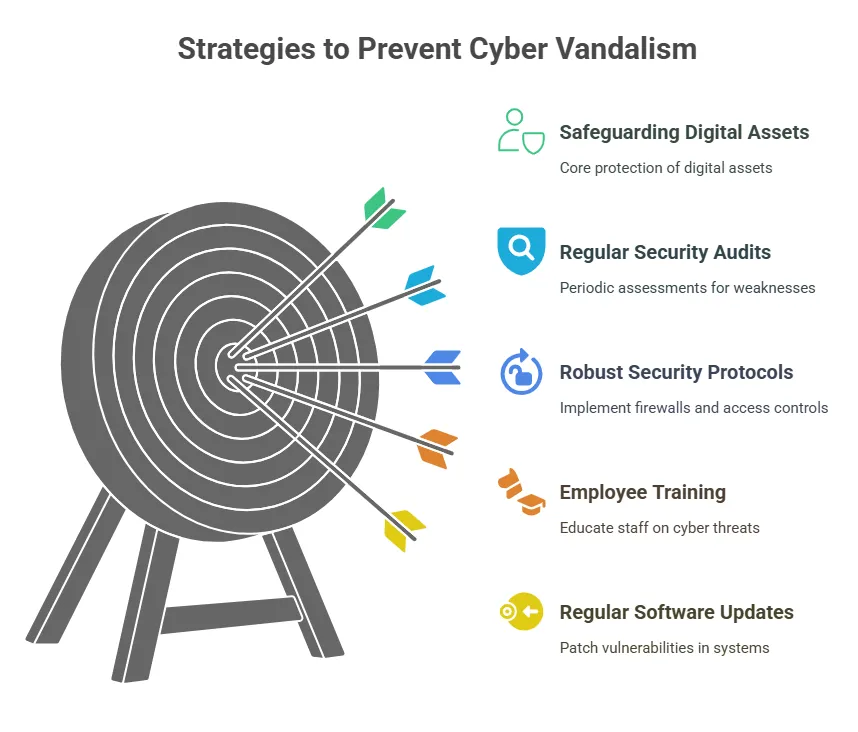
Strategies to Prevent Cyber Vandalism
Proactive measures are essential to safeguard your organization against cyber vandalism:
- Regular Software Updates: Ensure all systems and applications are up-to-date to patch known vulnerabilities.
- Employee Training: Educate staff on recognizing phishing attempts and other common attack vectors.
- Robust Security Protocols: Implement firewalls, intrusion detection systems and access controls.
- Regular Security Audits: Conduct periodic assessments to identify and address potential weaknesses.
By adopting these comprehensive strategies, organizations can significantly strengthen their defenses against cyber vandalism and safeguard their digital assets.
Responding to an Attack: Immediate Steps to Mitigate Damage
In the event of a cyber vandalism attack, swift action is crucial:
- Isolate Affected Systems: Prevent the spread of the attack by disconnecting compromised systems.
- Notify Stakeholders: Inform employees, customers and relevant authorities about the breach.
- Begin Incident Response Procedures: Activate your incident response plan to address the breach.
- Post-Incident Analysis: Conduct a thorough review to understand the breach and strengthen defenses.
Having a well-defined incident response plan can significantly reduce the impact of cyber vandalism.
Quick Guide: Cyber Vandalism Tactics and How to Respond
| Type of Cyber Vandalism | What It Looks Like | Immediate Response | Long-Term Prevention |
| Website Defacement | Offensive or altered content on your public site | – Take your website offline temporarily – Restore from backup |
– Use secure CMS platforms – Regular patching & updates |
| Data Deletion/Corruption | Missing, altered or unreadable customer or internal data | – Isolate affected databases – Initiate recovery process |
– Maintain off-site/cloud backups – Restrict data permissions |
| DoS Attack | Website or services become slow or unavailable | – Contact hosting provider – Activate DoS mitigation |
– Use anti-DDoS services – Scale hosting resources |
| Malware Insertion | System lags, pop-ups or unauthorized access to files/systems | – Disconnect from the network – Run antivirus/malware scan |
– Install endpoint protection – Conduct regular system audits |
Secure Your Organization with EXOS IT
At EXOS IT, we specialize in providing comprehensive cybersecurity services tailored to protect organizations from threats like cyber vandalism. Our team of experts will work with you to assess your current security posture, implement robust defenses and develop an incident response plan to ensure your organization is prepared for any cyber threat.
Contact EXOS IT today to schedule a consultation and take the first step towards securing your digital assets.
| Explore Other Leading Cybersecurity Services From EXOS IT | ||||
| 24×7 Monitoring | EDR | Dark Web Monitoring | DNS Filtering | Vulnerability Scanning |




